
How Secure Is It to Share Sensitive Personal or Business Information with a Virtual Assistant?
Share this post
Table of Contents
If you hire a virtual assistant (VA), it can totally change the way you handle your personal and business stuff. But a common question that pops up to many people is the security of sharing sensitive information: how safe is it to disclose such information to an outsider who is not in your office or home physically?
It is a legit worrying point. In the era when hacking and cyber threats are rampant, someone might feel uncomfortable and insecure in entrusting a virtual assistant with confidential information. Nevertheless, by using the right methods, the correct implements, and trust-building activities, one can still share sensitive data in a safe and secure way.
This article helps you understand the security aspects, what measures you and your VA need to take, and how KiteAssistant keeps you safe.
Why Sharing Sensitive Information is Necessary?
Virtual assistants to be effective in their work often require access to:
- Calendars and emails.
- Financial documents (invoicing, bookkeeping).
- Client contact details.
- Login credentials for software and tools.
- Personal identification information (for booking travel, appointments).
If the VA is not provided with some confidential information, his/her job will be so limited that it will be like not having a VA at all.
Security Concerns When Sharing Information with a VA.
- Data Theft or Misuse: Anxiety that the VA might take or disclose the confidential data.
- Unauthorized Access: The VA mistakenly or purposely gaining access to the areas that are off-limits for them.
- Phishing or Cyberattacks: Problems due to lack of security measures.
- Lack of Control: Not being able to oversee the way data is managed and stored.
Ways to Secure a Virtual Assistant to Work for You.
1. Thoroughly Examine Your Virtual Assistant.
- One good source of VA is KiteAssistant, which also does the checking of backgrounds and verifying of the credentials.
- Get references from the person or see the comments of the previous work.
- When carrying out the interview, ask security-related questions so as to gauge the candidate’s knowledge of the issue.
2. Secure Communication Methods.
- Don’t transmitting sensitive information through unsecured channels like traditional email or common messaging apps.
- Make use of encrypted services like Signal, ProtonMail, or Slack with 2-factor authentication (2FA).
3. Set Up Controls on Access.
- Only let them see what they absolutely have to – least privilege principle.
- With the help of password managers (LastPass, 1Password), you can give someone a password without showing the exact one.
- Instead of sharing the main login details for tools and software, create limited-access accounts.
4. Have Non-Disclosure Agreement (NDAs).
- Make sure the VA signs an NDA which clearly spells out confidentiality and consequences if there is a breach.
- This act not only formal setting but also giving legal backing.
5. Keep Updating and Checking Access.
- Regularly change your passwords.
- Check who has been accessing if your software keeps logs.
- Don’t delay in taking back the access rights when the agreement is over or you suspect that the data has been misused.
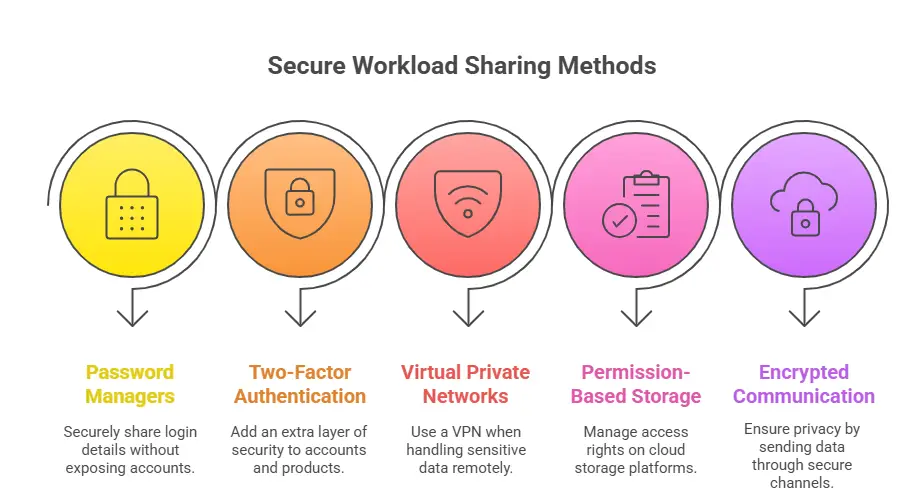
Methods and Norms for Secure Sharing a Workload.
- Password Managers: Checking and sharing of login details without exposure of accounts.
- Two-Factor Authentication (2FA): Additional security layer for accounts/product.
- VPNs: A Virtual Private Network can be used when working with sensitive data on the go.
- Permission-Based Cloud Storage: Google Drive, Dropbox allows users to manage the access rights of others.
- Encryption Communication: Privacy is ensured when data is sent over safe channels.
What Are The Measures KiteAssistant Takes To Keep Your Data Safe?
Here at KiteAssistant, we don’t take your privacy and data security lightly:
- Every single virtual assistant is vetted thoroughly and trained in data privacy before dropped with your project.
- Our whole onboarding process is secure and we communicate only through safe channels.
- Confidentiality agreements and clauses are standard practice.
- We perform regular audits and compliance checks.
Besides that, we give security guidelines and support to clients, thus they can always keep a high standard of security.
If You Suspect A Security Breach, What Steps Should You Take?
- Stop all interaction and communication with the VA immediately.
- Alter all passwords and make changes to your password manager.
- Inform clients or stakeholders who are affected if it is needed.
- Go through your security policies and fix the weak points.
If the breach is of a serious nature, you may also want to consider legal advice.
Take Away.
You can safely share sensitive personal or business information with a VA if you take proper security measures. First, inspect your VA thoroughly, then go on using secure means, limiting accessibility, and finalizing the confidentiality agreement. If everything is right, a VA becomes a trusted member of your team who saves time and makes you more productive, without you having to worry about your security.
We at KiteAssistant are all about your privacy and security from start to finish. Drop us a line and find out how we keep your data safe while you reap the benefits of a professional virtual assistant.
Nebadita
Table of Contents
You May Also Like
Virtual Assistants That Enhance Your Work and Life
Kite offers a fully managed, dedicated virtual assistant solution that helps startups and SMBs delegate time-consuming but essential tasks—so they can focus on what truly matters.





